The subject of the interrelation of threats in the fields of information and communication technologies and nuclear weapons is gradually becoming one of the dominant topics in current international security issues. In early summer 2019, a group of researchers working under the auspices of the Nuclear Threat Initiative (NTI) presented the Russian version of the “Nuclear Weapons in the New Cyber Age” report prepared by the Cyber-Nuclear Weapons Study Group (hereinafter referred to as the NTI Report). Russian assessments of the proposals put forward by American experts may contribute to finding constructive solutions that may be ultimately transferred to international communication platforms.
Understanding the Threats
The NTI Report is structured very logically and succinctly. The authors give specific examples using formalized scenarios and demonstrate the practical dimension of specific threats and their consequences. This is followed by concrete proposals. On the whole, this approach is conducive to understanding the essence of certain phenomena and is useful both for experts in the area under consideration and for the general public. Moreover, one would like to think that decision-makers in various countries will be interested in the problems considered.
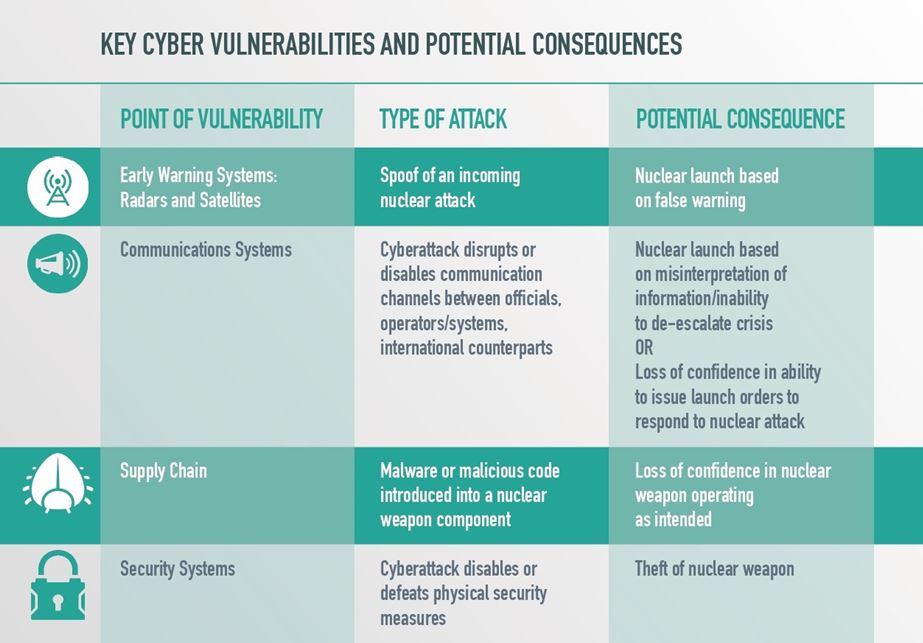
The authors considered four “illustrative scenarios”:
- Scenario 1: Warning systems provide false indications of a nuclear attack during a crisis.
- Scenario 2: A cyberattack disrupts communications between officials, operators and nuclear systems, and/or international counterparts in a potential crisis.
- Scenario 3: An adversary introduces a flaw or malevolent code into nuclear weapons through the supply chain or otherwise in a way that could compromise the effectiveness of those weapons
- Scenario 4: An adversary is able to achieve unauthorized control of a nuclear weapon through cyber-assisted theft and/or defeating of security devices.
These scenarios look quite realistic. We will not go into detailed descriptions (or, more precisely, retellings) of them. A brief summary is given in Figure 1.
Fig.1
At the same time, we will note that each scenario has an element of simplification, which is generally justified from the point of view of the research objectives. An important clarification should be made, at least for the first scenario. An early warning system comprises many elements, and it is highly improbable that the decision to deliver a retaliatory strike will be made on the basis of a single sub-system. The probability of the “entire set” malfunctioning or being hacked and providing the exact same information appears to be very low. At the same time, when nuclear powers are in a crisis that has an obvious military aspect to it, the threat of a hastily made decision will also increase.
A Search for Solutions
The authors of the NTI Report propose the following three guiding principles that should be taken into account when developing approaches to minimizing the risk of cyber threats against nuclear weapons:
- The United States will continue to require a safe, secure, and reliable nuclear deterrent as long as nuclear weapons remain a central element of its security strategy.
- Technical measures alone are unable to completely eliminate the cyber threat to nuclear weapons.
- The cyber challenge is global, and a unilateral approach is not sufficient.
These principles appear to be quite sound and constructive. Item 1 is certainly reasonable for Russia and for other nuclear powers.
Maybe such statements should be also reflected in bilateral (or even multilateral) declarations on international security issues and strategic stability. Naturally, conditions should emerge first for such declarations.
The experts make several very specific proposals, which are grouped as follows:
- reducing the risk of launch as a result of miscalculation;
- reducing risks to the nuclear deterrent;
- reducing the risk of unauthorized use;
- taking a global approach to the cyber threat to nuclear weapons systems.
On the whole, this approach seems logical, but the feasibility of these proposals is questionable.
Certainly, the key task shared by all nuclear powers is to guarantee the impossibility of accidentally interfering with nuclear weapons and related infrastructure through information and communication technologies. What is problematic is the attitude of various states to interference that is deliberate, i.e. intentionally carried out by government services against probable adversaries. This contradiction sharply limits the room for joint action to minimize threats.
In particular, the recommendation contained in the NTI Report on bilateral and multilateral steps towards developing certain new rules of behaviour in cyberspace are unlikely to be fully implemented. This is primarily due to one of the key features of cyber weapons: the impossibility of reliably ascertaining the adversary’s target, even if the malware itself has been detected. Identical cyber weapons can be used to collect information and interfere with the systems into which the malware has been introduced.
Unilateral and Multilateral Approaches
At the same time, much can be done in the context of unilateral measures to minimize cyber threats.
It would seem that the most important task in this area is the training of qualified military personnel for the nuclear forces. Excellent knowledge of relevant weapons and military equipment, as well as the rules of operation in any situation and basic “digital hygiene” will evidently contribute to the overall reduction of threats.
Comprehensive rules and regulations for protecting equipment from external interference already exist. However, given that individual components are purchased from foreign manufacturers (this problem is relevant for both Russia and the United States), there is still danger of hardware implants. Let us hope that personnel of the relevant departments in the military and the special services have the necessary qualifications to detect such threats.
At the same time, certain national measures for enhancing the cyber protection of the nuclear weapons infrastructure should be compiled into some sort of “best practices” collection. Perhaps P5 countries (China, France, Russia, the United Kingdom, and the United States) could prepare some handbooks to be distributed, for instance, as part of a Non-Proliferation Treaty Review Conference. This would to some extent demonstrate the responsible approach of recognized nuclear powers to current issues related to nuclear weapons.
As we have mentioned before, developing a relevant section in the Glossary of the Key Nuclear Terms could be a useful step, as fine-tuning the Glossary is supposedly still on the agenda. A dialogue based on a uniform conceptual and categorial framework leads to negotiations being more effective. At the same time, forming a uniform terminology should not be viewed as a trivial task. The solution of this task requires both political will and a deep understanding of the subject of negotiations. And still, even if such procedures do not have a positive outcome, such communications promote an improved understanding of assessments, approaches and paradigms among partners.
We should remember the Joint Statement of the Russian Federation and the People’s Republic of China on strengthening global strategic stability today, which envisages, among other things, a joint “analysis of the regulation of new strategic security dimensions” related to the “possible impact of achievements in science and technology.” Moreover, Russia and China consider it appropriate to conduct a multilateral study of the relevant problems and their legal regulation on the basis of the United Nations.
Expanding the Context
As we have already mentioned, the crucial feature of cyber weapons (that kind of links it with “kinetic” weapons, primarily strategic weapons) is that the delivery vehicle and the payload are two different things: the same product can be used to introduce malware intended for monitoring and spying, as well as for control hacking and disabling.
Maybe classifying cyber weapons by hostile impact type can create conditions for searching for points of contact between various countries and international organizations. In general, the task of formalizing and coordinating definitions is one of the most complicated stages of any negotiation process, and a key stage that determines the success of the negotiations and the prospects for adapting the agreements to the rapidly changing reality against the backdrop of the scientific and technological progress.
As for deliberate cyberattacks that may be of interest to states that have the requisite capabilities, we should take note of the opinion of the UK-based Chatham House, which draws attention to the complex dynamics of military-political relations in the event of a further escalation in rhetoric concerning cyberattacks preventing combat missile launches as part of the so-called “left of launch” concept, which the General Staff of the Armed Forces of the Russian Federation calls “pre-start intercept.” The problem is that the hypothetical “Party A,” fearing an attack of such kindby “Party B,” may decide to use weapons at the early stages of a conflict. And if “Party B” is bluffing, then calling its bluff may result in the “failure” of the deterrent tactic. If “Party B” is confident in its supreme cyber capabilities, then its actions can easily become overconfident and result in a “hot” conflict.
Strictly speaking, the problem of the “rules of the game” in cyberspace is important in and of itself, without being tied to nuclear weapons. For instance, attempts can be made to train “cyber soldiers” to follow the rules of international humanitarian law, as, for instance, Professor Götz Neuneck from the Institute for Peace Research and Security Policy at the University of Hamburg (IFSH) suggests. And the specific content of such concepts as “proportionality” and “military necessity” when applied to cyberspace requires additional research. Joint international exercises, including those related to nuclear systems, ideally with the participation of “probable adversaries,” could be a useful event in this area. Thus, states could gain some experience of acting in a simulated combat situation and gain experience of interaction through emergency communication channels, which is of crucial importance.
Safe Communication Lines
For decades, information and communication technologies have been developing at breakneck speed, and the militarization of cyberspace accompanies these processes. In general, any technological changes result in new threats, and “Neo-Luddism” will hardly be a suitable cure for such threats. “Nuclear abolitionists” are unlikely to achieve their goals in the foreseeable future either: we are seeing a return to the international rivalry of great powers, and nuclear weapons are one of the principal elements confining death and destruction in the course of this rivalry within relatively moderate bounds.
The only way to preserve strategic stability and prevent catastrophic consequences from the incorrect use of nuclear weapons is to perform an in-depth analysis of the impact that new technologies have on the relevant systems. This analysis should be as open as possible and involve an element of international dialogue at both the state and expert levels. At the same time, it is necessary to “increase literacy” in information and communication technologies and nuclear weapons (and their control systems) both among military personnel and among civilian specialists and decision-makers. The NTI Report and the subsequent communication activities of its authors are a step in the right direction, especially since representatives of the Ministry of Defence of the Russian Federation attended the presentation of the report at the Institute for U.S. and Canadian Studies of the Russian Academy of Sciences.